Struggling to find the perfect remote access solution for your IoT devices? Mastering IoT remote SSH setup is no longer optional; it's an absolute necessity for efficient device management and robust security in today's interconnected world.
The sheer number of Internet of Things (IoT) platforms available can indeed feel like navigating a complex maze. Selecting the right one is paramount, and the ideal platform extends beyond merely providing remote SSH access. It must also champion ease of use, boast scalability to accommodate your growing network, and incorporate robust security features to protect your valuable data. The quest to unearth the best free remote SSH solutions for your Raspberry Pi projects, or any IoT endeavor, can feel daunting, but the reward streamlined control and fortified security is well worth the effort. As IoT ecosystems continue their relentless expansion, the challenge of maintaining secure remote access becomes progressively more complex. This necessitates a deep dive into understanding and implementing the best practices for IoT remote SSH connections, which can significantly enhance your device management capabilities while simultaneously maintaining robust security standards.
| Category | Information |
|---|---|
| General Information | |
| Topic | IoT Remote SSH Access |
| Definition | Securely accessing and managing IoT devices remotely using SSH (Secure Shell) protocol. |
| Importance | Enables efficient device management, troubleshooting, and updates from anywhere. Crucial for security and control in IoT deployments. |
| Key Components | |
| SSH Server | Software running on the IoT device that allows remote connections. (e.g., OpenSSH) |
| SSH Client | Software used to connect to the SSH server on the IoT device. (e.g., PuTTY, MobaXterm, Terminal) |
| Authentication | Methods for verifying the identity of the user connecting to the IoT device (e.g., passwords, SSH keys). |
| Networking | Network configuration required for the SSH client to reach the IoT device (e.g., IP address, port forwarding). |
| Technical Details | |
| Protocol | SSH (Secure Shell) |
| Port | Default: 22 (can be changed for security) |
| Encryption | Uses strong encryption algorithms (e.g., AES, ChaCha20) to protect data transmitted over the connection. |
| Security Considerations | |
| Password Security | Use strong, unique passwords. Consider disabling password-based authentication and using SSH keys instead. |
| SSH Key Authentication | Generate and use SSH key pairs for more secure access. Store private keys securely. |
| Firewall | Configure firewalls to allow SSH access only from trusted networks/IP addresses. |
| Regular Updates | Keep SSH server software up-to-date to patch security vulnerabilities. |
| Tools | |
| OpenSSH | A widely used, open-source SSH implementation. |
| PuTTY | A free SSH and Telnet client for Windows. |
| MobaXterm | An enhanced terminal for Windows with X11 server, tabbed SSH client, network tools, and more. |
| Raspberry Pi Specifics | |
| Default Configuration | Raspberry Pi OS often comes with SSH server pre-installed but disabled. |
| Enabling SSH | Can be enabled via `raspi-config` or by creating an empty file named `ssh` in the `/boot/` partition. |
| User | Default username: `pi`, Default password: `raspberry` (should be changed immediately). |
| Ubuntu Linux Specifics | |
| Installation | Install OpenSSH server using `sudo apt install openssh-server`. |
| Configuration File | Configuration file located at `/etc/ssh/sshd_config`. |
| Best Practices | |
| Change Default Port | Change the default SSH port (22) to a higher, non-standard port to reduce automated attacks. |
| Disable Root Login | Disable direct root login via SSH for enhanced security. |
| Limit Login Attempts | Use `fail2ban` to automatically ban IP addresses that make too many failed login attempts. |
| Regular Audits | Regularly audit SSH configuration and logs to identify and address potential security issues. |
| Use Cases | |
| Remote Monitoring | Monitor the status and performance of IoT devices remotely. |
| Remote Configuration | Configure and update IoT device settings without physical access. |
| Troubleshooting | Diagnose and resolve issues on IoT devices remotely. |
| Data Collection | Securely collect data from IoT devices. |
| Related Technologies | |
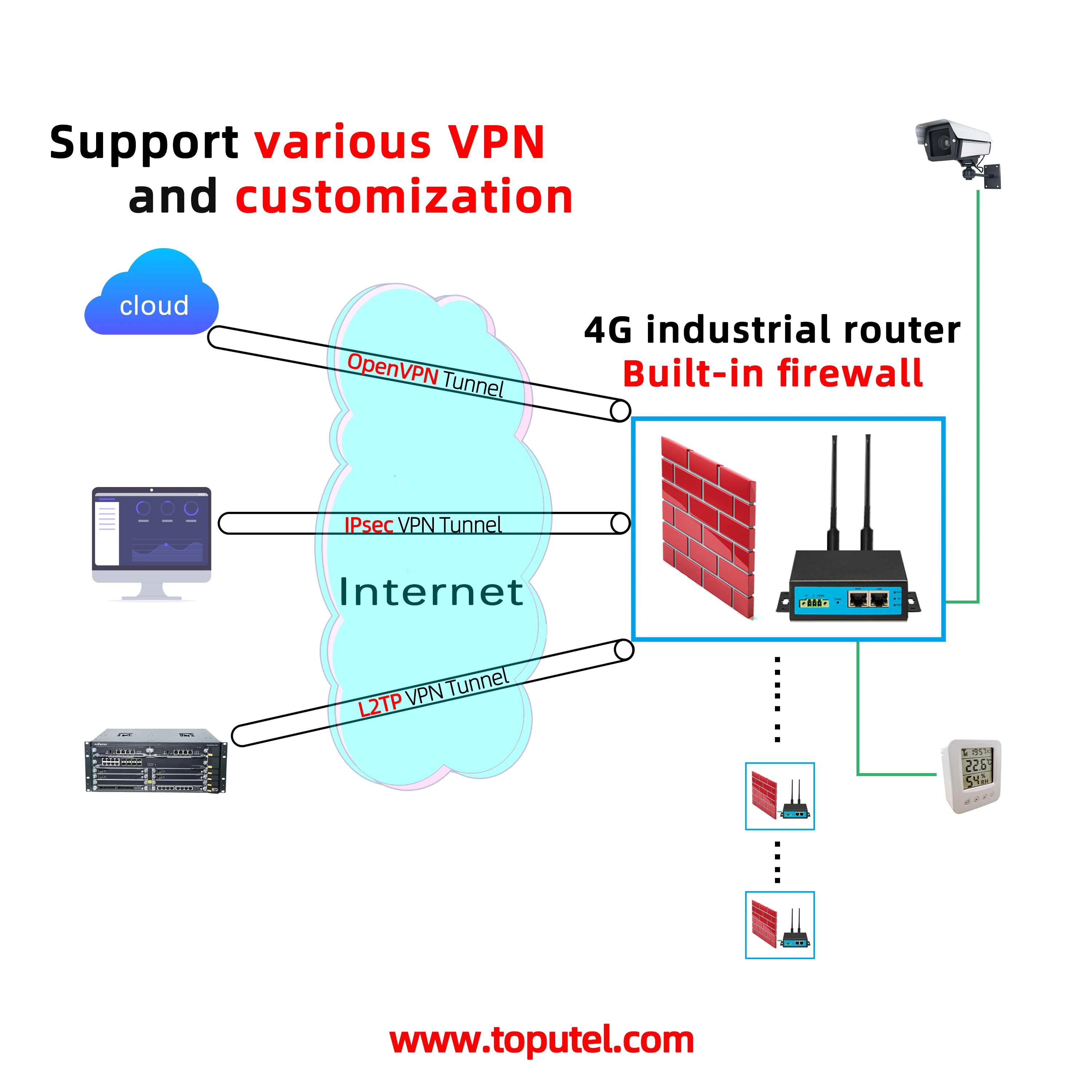
| VPN (Virtual Private Network) | Provides a secure, encrypted tunnel for accessing IoT devices over the internet. |
| IoT Platforms | Cloud-based platforms that provide comprehensive management and security features for IoT devices. (e.g., AWS IoT, Azure IoT Hub) |
| Reference Website | SSH.com |
- Tony Miranne Joy Manganos Exhusband Net Worth More
- Mydesi More Connecting The South Asian Diaspora Today